v1g1lance.netlify.app
Asa Generate Ssh Key Asdm
CSR Creation for Cisco Adaptive Security Appliance 5500. If you already have your SSL Certificate and just need to install it, see SSL Certificate Installation for Cisco ASA 5500 VPN. How to generate a CSR in Cisco ASA 5500 SSL VPN/Firewall. From the Cisco Adaptive Security Device Manager (ASDM), select 'Configuration' and then 'Device Management.' Sshexchangeidentification: Connection closed by remote host Fail to establish SSH session because RSA host key retrieval failed. Source: Link Now you need to configure the authentication piece of remote access for the connection. On the left side select Users/AAA- AAA Access. Under the Authentication Tab, Check SSH and select Server Group: LOCAL. This will allow you authenticate with a local user.
CSR Creation for Cisco Adaptive Security Appliance 5500
Besides allowing the permitted hosts to SSH to the ASA, you need to define RSA keys for the secure connection. In the CLI: crypto key generate rsa. For these key to work, you should have a hostname/domain-name configured on the ASA as well (unless you configure a dedicated RSA keys). How to configure remote access for ASDM and SSH for an ASA 5505. You will also have to generate the ssh key. Type the following from ASDM or through a console. Sep 06, 2014 Secure Shell (SSH) on the other hand uses port 22 and is secure. SSH uses public key cryptography to authenticate remote user. You can configure SSH access in Cisco ASA device using the steps shown here. Apr 17, 2014 Enable SSH and TELNET login on Cisco ASA 7.x inside Interface. Presented in order to generate the same RSA keys with ASDM. New in order to add a default key.
If you already have your SSL Certificate and just need to install it, see
SSL Certificate Installation for Cisco ASA 5500 VPN.
How to generate a CSR in Cisco ASA 5500 SSL VPN/Firewall
From the Cisco Adaptive Security Device Manager (ASDM), select 'Configuration' and then 'Device Management.'
Expand 'Certificate Management,' then select 'Identity Certificates,' and then 'Add.'
Select the button to 'Add a new identity certificate' and click the 'New..' link for the Key Pair.
Select the option to 'Enter new key pair name' and enter a name (any name) for the key pair. Next, click the 'Generate Now' button to create your key pair.
Change the key size to 2048 and leave Usage on General purpose.
Next you will define the 'Certificate Subject DN' by clicking the Select button to the right of that field. In the Certificate Subject DN window, configure the following values by selecting each from the 'Attribute' drop-down list, entering the appropriate value, and clicking 'Add.'
CN - The name through which the firewall will be accessed (usually the fully-qualified domain name, e.g., vpn.domain.com).
OU - The name of your department within the organization (frequently this entry will be listed as 'IT,' 'Web Security,' or is simply left blank).
O - The legally registered name of your organization/company.
C - If you do not know your country's two digit code, find it on our list.
ST - The state in which your organization is located.
L - The city in which your organization is located.
Please note: None of the above fields should exceed a 64 character limit. Exceeding that limit could cause problems later on while trying to install your certificate.
Next, click 'Advanced' in the 'Add Identity Certificate' window.
In the FQDN field, type in the fully-qualified domain name through which the device will be accessed externally, e.g., vpn.domain.com (or the same name as was entered in the CN value in step 5).
Click 'OK' and then 'Add Certificate.' You will then be prompted to save your newly created CSR information as a text file (.txt extension).
Remember the filename that you choose and the location to which you save it. You will need to open this file as a text file and copy the entire body of it (including the Begin and End Certificate Request tags) into the online order process when prompted.
After you receive your SSL Certificate from DigiCert, you can install it.
See SSL Certificate Installation for Cisco ASA 5500 VPN.
Cisco SSL Certificates, Guides, & Tutorials
Buy NowLearn MoreGenerating a CSR for Issuance of an SSL Certificate on a Cisco ASA 5500 VPN/Firewall
How to generate an SSL Certificate Signing Request for your ASA 5500 SSL VPN
This guide will walk you through the basics of hardening SSH access to your Cisco ASA firewall using ASDM. If you're like me, you'd rather have a GUI than spending the day Googling CLI commands.
4 Steps total
Step 1: Login to ASDM
Step 2: Change the default allow SSH version from 1 to 2
Go to Configuration > Device Management > Management Access > ASDM/HTTPS/Telnet/SSH
Ssh with private key. Under SSH Settings, change the value of 'Allowed SSH Version(s)' from 1 to 2.
Step 3: Change the default Diffie-Hellman group from 1 to 14
Remain in Configuration > Device Management > Management Access > ASDM/HTTPS/Telnet/SSH
Under SSH Settings, change the radio toggle of 'DH Key Exchange' from Group 1 to Group 14.
Step 4: Lock down SSH access to the firewall
Remain in Configuration > Device Management > Management Access > ASDM/HTTPS/Telnet/SSH
Under 'Specify the addresses of all hosts/networks which are allowed to access the ASA using ASDM/HTTPS/Telnet/SSH', you should add the static IPs of the devices or servers you wish to access the firewall from.
Click Add on the right.
Select the radio button next to SSH.
Select 'Inside' as the interface.
Enter the static IP of the device/server.
Enter 255.255.255.255 as the subnet mask.
Click OK.
Repeat for all remaining devices/servers or specify any outside IPs which are static that require remote access.
WARNING: If your firewall has 0.0.0.0 'any' enabled by default, make sure you save your changes by adding your static IP first before deleting the 'any' entry. Otherwise, your session will disconnect.
You may repeat the last step for hardening access to ASDM as well.
Asa Generate Ssh Key Asdm Code
3 Comments
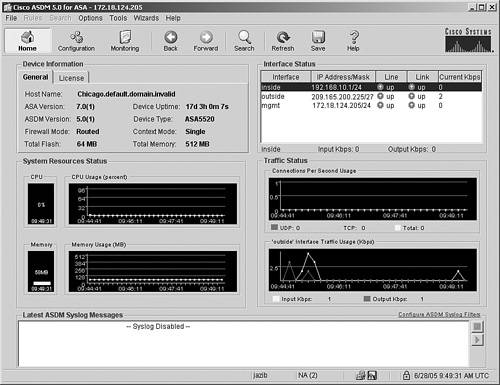
Cisco Asa Asdm Configuration
- Sonoraalexthompson4 Oct 16, 2018 at 06:51pm
Thank you for the guide! For accessing the ASA through SSH, what devices would you recommend connecting from (a server, etc) from a security standpoint?
- Ghost Chilistarg33ker Oct 16, 2018 at 06:56pm
I only connect to the ASA from our Hyper-V host.
- Sonoraalexthompson4 Oct 16, 2018 at 07:02pm
That's a good idea! I shall have to work on implementing it at my workplace.